Basic Auth Password
When you have organizational assets present online, you definitely worry about their security. Ensuring that resources and databases are not in the wrong hands can start with basic authentication. Designed for HTTP users, it is the basic schema for validating a request reaching the server.
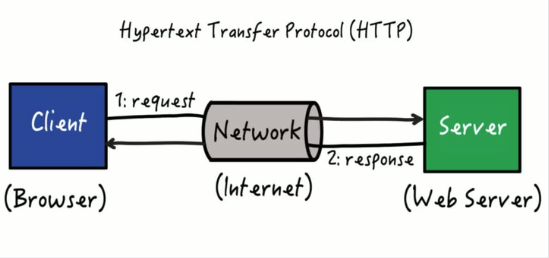
The "Basic" HTTP authentication scheme transmits credentials as user-Id/password pairs, encoded using base64. As the user-Id and password are passed over the network as clear text (it is base64 encoded, but base64 is a reversible encoding), the basic authentication scheme is not secure. HTTPS/TLS should be used with basic authentication. Without these additional security enhancements, basic authentication should not be used to protect sensitive or valuable information.
What type of Authentication and security does Easee provide?
Easee provides TLS with Basic Authentication and not TLS with Client Side Certs. Transport Layer Security (TLS) is the successor protocol to (Secure Sockets Layer) SSL, an improved version of SSL. It works in much the same way as the SSL, using encryption to protect the transfer of data and information. The two terms are often used interchangeably in the industry although SSL is still widely used, however, there is no question that TLS is better than SSL.
HTTPS today uses Transport Layer Security or TLS. TLS is a network protocol that establishes an encrypted connection to an authenticated peer over an untrusted network.

How it works?
Used widely in HTTPS-based communication, the basic method is the means of authenticating end-users before granting access to resources or communication. For the same, intended users are instructed to deliver primary credentials like user names and login passwords.
In HTTP authentication, you have a header, Authorization, and its value (the header name is rather unfortunate because it is usually used for authentication and not as often for access control, aka authorization). The Authorization header value is what is used by the server to perform authentication, and it is composed (usually) of three tokens:
-
- An HTTP authentication scheme name, followed by
-
- white space (almost always a space character), followed by
-
- The scheme-specific text value.
One common HTTP authentication Scheme is the Basic scheme, which is very... well... basic. The scheme-specific text value is simply the following computed value:
- The scheme-specific text value.
String concatenated = username + ":" + raw_password;
String schemeSpecificTextValue = base_64_encode(concatenated.toCharArray());So you might see a corresponding header look like this:
Authorization: Basic QWxhZGRpbjpvcGVuIHNlc2FtZQ==The server knows how to parse the value. It says "Hey, I know the Basic scheme, so I'm going to take the trailing text value, base64 decode it, and then I'll have the username and submitted password. Then I can see if those values match what I have stored."
And that's essentially Basic authentication. Because this scheme in particular includes the submitted raw password base64 encoded, it is not considered secure unless you use a TLS connection. TLS guarantees (mostly) that prying eyes can't intercept the headers (e.g. via packet inspection) and see what the password is. This is why you should always use TLS with HTTP Basic authentication. Even in company intranet environments.

Try to think of it this way: When you are logging in to any website using SSL, you are most likely passing the password in plain-text over HTTPS.
The only difference that Basic-Auth makes is that user-Id/password is passed in the request headers instead of the request body (GET/POST).
Requirements
The password SHALL be stored in the AuthorizationKey Configuration Key. Minimal 16-bytes long, It is strongly advised to be randomly generated binary to get maximal entropy. Hexadecimal represented (20 bytes maximum, represented as a string of up to 40 hexadecimal digits).
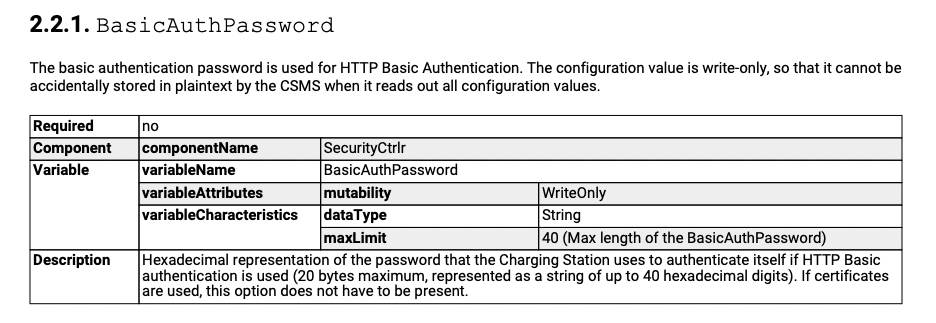
Sequence Diagram
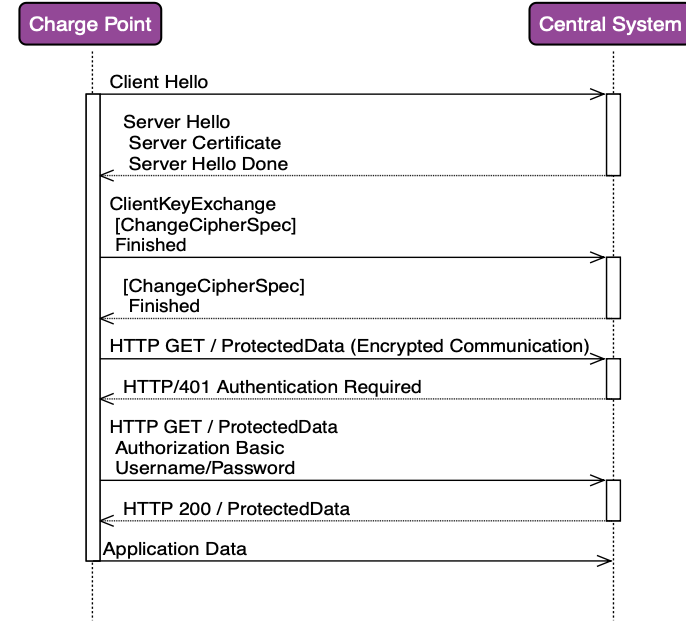
Sequence Diagram: TLS with Basic Authentication sequence diagram
Updated 11 months ago
